Let your business experience an expert thrust
A small percentage of organization perhaps can confidently say they have a high maturity of the TPRM program. A sizable percentage of organization are at a nascent stage with relatively low maturity level or are struggling to improve the maturity level of the TPRM program due to inherent challenges of the program.
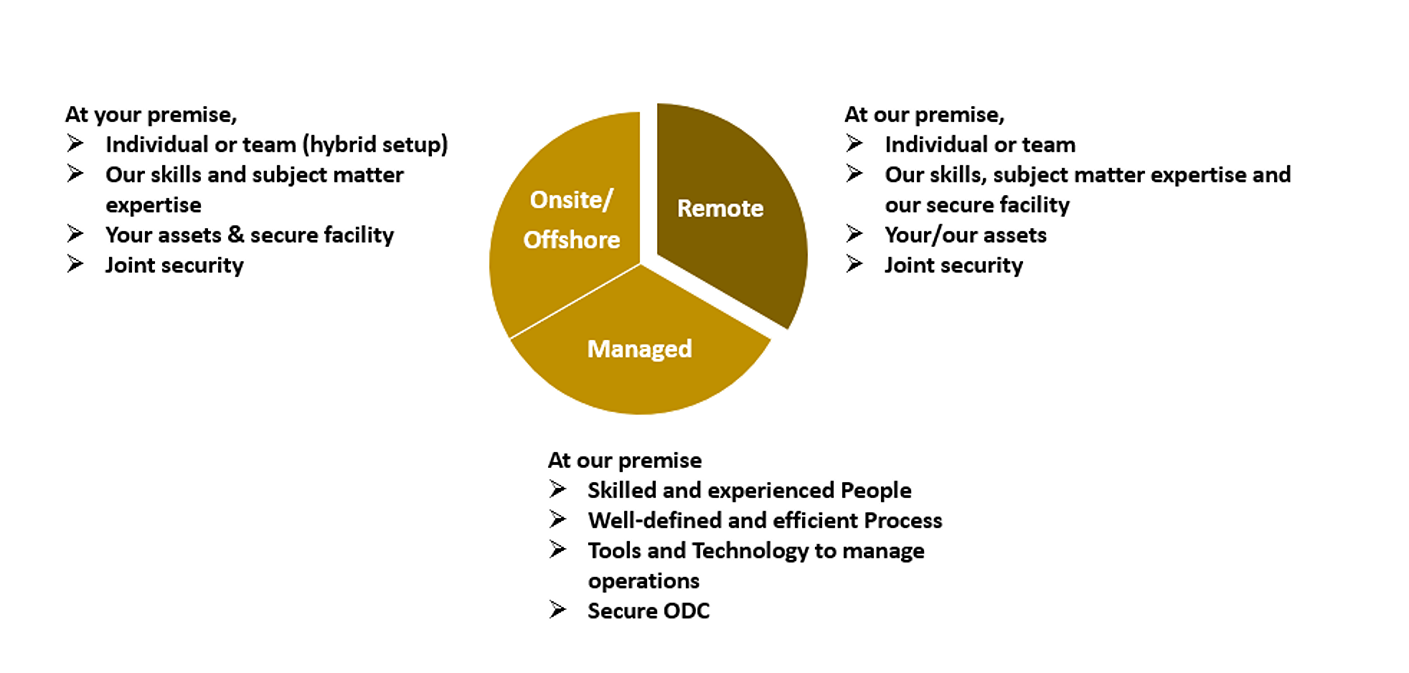
IMPLEMENTATION, CONSULTING & MANAGED SERVICES
Defentrix professional services team can help you in this journey to achieve the desired maturity level. We work with clients who need help to

Build a functioning TPRM program from scratch

Improve the operating efficiency and maturity of their program

Solve complex challenges in achieving the TPRM goals of your program

Fulfil the skill gap to ensure seamless operations
We rely on our security and industry experts with over 15 years of experience in Information Security and managing Third Party Risk Management (TPRM). We understand the goals, challenges and expected outcomes that your executive c-suite wants and deliver in the best possible way so that you succeed in achieving your goals and objectives. We are excited to be a part of your journey and as a valued partner for years to come.
1. Get to know your Maturity Level (Where you stand, allows you to see further)
Evaluate current maturity level and key program pillars that support the lifecycle and understand future state. We work with you and support you in creating a strategic plan to achieve TPRM objectives as per the industry benchmark
2. Assess and Build the essential elements of the program (Key ingredients of the recipe)
Augment or optimize the program in line with organization goals and objectives. We help you overcome the pain areas, and build a scalable and optimal model so that you can focus more on risks and less on the operating challenges
3. Balance operating model in line with industry standards (Supply vs Demand)
Assess the operating model and deduce areas of improvement. Enhance operating efficiency by
- Balance across Process, People and Technology to align with the program objectives
- Effective stakeholder management
4. Contract Management (Lay strong ground rules)
Enhance the lifecycle of contract management with the best practices and a strategy that increases building the relationships with Third Parties
5. Continuous Monitoring (Get your arms around it)
Our TPRM experts provide excellent strategies and techniques to address and manage the challenges and align with the objectives of continuous monitoring. Create a balance between actively monitoring and stakeholder reporting while keeping the risk at the minimum
6. Off-boarding (Saying Good Bye’s was never easy, but it is now)
We work with you to create an off-boarding strategy and implement a workflow that intertwines the other related steps of the onboarding that will allow you to have an oversight on the effective off-boarding process, practice reporting and exercise contract clauses meeting the ultimate objective of reducing risk
We help you find your way to navigate through the intricate design of complex operations to figure out the best way to operate and report.

Worried about your Information Security and TPRM?
Contact us today for complete consulting and implementation of Information Security
Latest Resources
2024 Leadership Vision for Third Party Risk Management (TPRM)
CISOs have a diverse array of rapidly evolving priorities, threats, demands, regulatory pressures, and technology changes to address. Leaders need a structured approach to today's security and risk landscape covering third-party risk. This blog sheds light on...
TPRM Awareness, upskill and cross skill
The security world is very diversified, with the majority of the organizations practicing defensive security while a few have adopted offensive security as well. Security professionals need to keep abreast with developments in Third Party Risk Management space and...
DPDP Act 2023 (India) and Third Party Risk Management (TPRM)
The impact of globalization, social networking, outsourcing, adoption of cloud and technologies, cross border data flows are some of the prominent reasons why data collection and sharing is ubiquitous in this digital age. Many countries have realized the importance of...



