Guarding you right at the doorstep
When it comes to Third Party Risk Management (TPRM), evaluating your risk right at the entry-level becomes crucial, understanding the inherent risk at the get-go enables leaders to consciously take risk-informed decisions thus reducing inherent risk. Selecting Third Parties with sub-optimal security standards increases the time and effort to perform Due Diligence. Defentrix is your one-point source for complete TPRM solution which covers Third Party pre-onboarding activities professionally covering stringent processes and customized qualification criteria. As per your need, we tailor pre-onboarding services whether it’s a complete or standalone solution.

Quick evaluation of shortlisted Third Parties against your security standard as part of pre-onboarding criteria

Analyze Inherent Risk to evaluate and gauge their security governance standards and determine risks that Third Party brings to your organization.

Classify in respective Tiers based on Risk exposure and impact, especially with Third parties that manage regulated data
Common Challenges Faced by the Businesses
Companies often face the challenge to successfully vet the qualifying security criteria without an accurate initial assessment, be it evaluating a handful of Third Parties to meet a business requirement or solve a business challenge. Thus, running into multiple risks at a later stage which increases TAT for successful onboarding. Pre-onboarding exercise helps in identifying those Third Parties which meet your baseline for security standards thus saving time and energy chasing Third Parties for remediation.
What we do for you in the TPRM Pre-Onboarding Phase
Capture key details on prospective Third Parties and evaluate them from a security governance standpoint
Key details about the Third Party (Region, Offerings, Products/Services) – it must be noted that certain “Notified” countries will be inherently High risk (such as Cuba, Iran, Russia etc.)
- Data Exposure, Technology & Integration (On-premise/Cloud)
- Compliance to applicable security, privacy, health, financial regulations, local and federal laws
- Review security documentation – ISO certification (e.g. 27001, ISO 27018/19, ISO 27036), SOC2, PCI-DSS, HIPAA, CAIQ, NIST
- Past security incidents or breaches suffered by their clients
- Annual spend and Security rating of the Third Party
- Reliance on the Third Party offerings
Process gathered information to calculate the Inherent Risk and rightly classify the Third Party category
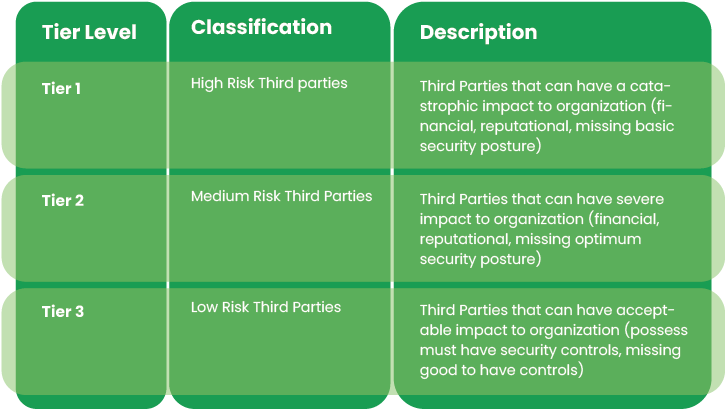
Tiering of Third Parties (see below) is commonly classified into 3 Tiers but organizations can define additional tiers as per requirement
- Classify the applicable types of Inherent risks (e.g., Compliance Risk, Operational Risk, Strategic Risk, Reputational Risk, Information Security Risk, Financial and Credit Risk, Geopolitical Risk, Concentration Risk, Transactional Risk)

Defentrix Offering
Build a TPRM security baseline document as a ready reckoner for Business & Third Parties
- Inputs from the Security Leadership, Internal Standards and TPRM function
- Align the baseline to the objective of TPRM program
Tiering of Third Party based on the Inherent Risk rating
- Capture key details
- Region, products/services offered
- Type of data exposure, technology and integration
- Applicable regulations and laws (local and federal)
- Security governance documentation
- Tier based evaluation of inherent risk (Tier 1,2,3 etc.)
- Determine and establish the potential impact and type of applicable risks (Compliance Risk, Operational Risk, Strategic Risk, Reputational Risk, Information Security Risk, Financial and Credit Risk, Geopolitical Risk, Concentration Risk, Transaction Risk)
Target mitigation of Inherent risk exposure before onboarding
- Prioritize identified risk and evaluate viable controls
- Validate compensating controls to minimize risk exposure to acceptable level
Gain inputs to security due diligence
- Determine the variation level of assessment (e.g., Comprehensive, Moderate or Lite)
- Proactive communication to support cross-functional teams

Guidance to Procurement to follow defined approach while processing onboarding requests
- Guidelines or playbooks facilitating BAU
- Uniform tracking of SLA, process and escalation procedure
Define metrics to track the volume, effort, SLA, approvals, rejections, no. of risks observed etc.
- Determine operational load, capacity and forecast to manage resources
-
Track cross function activities with pre-defined SLAs
Custom reports that helps with statistics and trends
- Periodic reports for senior management
- Trends for executive and board
Benefits of Associating with Defentrix Third Party Pre-Onboarding Services
Establish accurate trigger points for security due diligence
Contribute to shorter Turn-around-Time (TAT) to perform end-to-end assessments

Worried about your Information Security and TPRM?
Contact us today for complete consulting and implementation of Information Security
Latest Resources
2024 Leadership Vision for Third Party Risk Management (TPRM)
CISOs have a diverse array of rapidly evolving priorities, threats, demands, regulatory pressures, and technology changes to address. Leaders need a structured approach to today's security and risk landscape covering third-party risk. This blog sheds light on...
TPRM Awareness, upskill and cross skill
The security world is very diversified, with the majority of the organizations practicing defensive security while a few have adopted offensive security as well. Security professionals need to keep abreast with developments in Third Party Risk Management space and...
DPDP Act 2023 (India) and Third Party Risk Management (TPRM)
The impact of globalization, social networking, outsourcing, adoption of cloud and technologies, cross border data flows are some of the prominent reasons why data collection and sharing is ubiquitous in this digital age. Many countries have realized the importance of...



